 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
| Last Updated: Thu Jul 14 11:51:52 UTC 2016 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
 |
| Last Updated: Thu Jul 14 11:51:52 UTC 2016 |
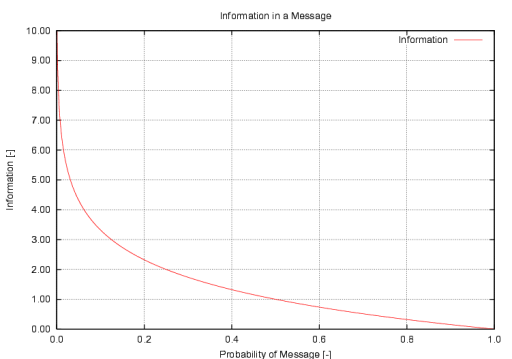
| Information Theory Research (Currently Active) Information Theory, Strategy, Hypergames, Social Systems, Biological Systems, Cognitive Cycles |
|||||||||||||||||||||||||||||||
 |
|||||||||||||||||||||||||||||||
|
Introduction |
|||||||||||||||||||||||||||||||
|
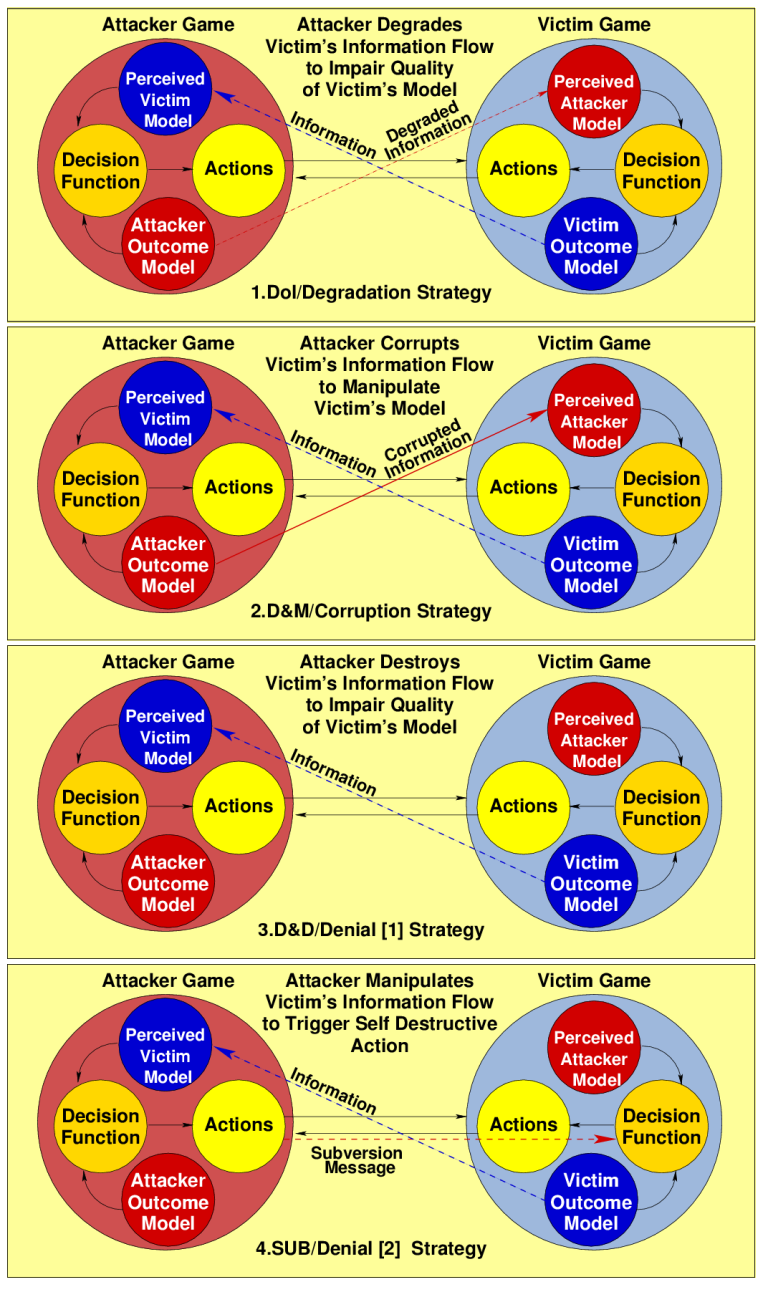
The four canonical
strategies
of deception provide a rigorous and
mathematically
supportable theoretical basis for the analysis of a wide range of
problems involving deceptions and other forms of manipulating
information in survival contests. These strategies, rooted in Shannon's
information theory and game theory, have been shown to
provide a robust model for dealing with problems spanning biological,
social, computing and other systems.
Hypergames are meta-games which permit modelling of deception and misperception. This area of research has been largely dormant since the 1980s. Current research involves exploration of the utility of hypergames in modelling social systems, biological systems and the evolutionary implications of hypergames. Large social systems such often exhibit unusually complex behaviours. Historical models for the latter include Lanchester's exchange rate equations, or the application of Metcalfe's Law to the modelling of networked systems. Further basic research is needed to fully quantify the properties of such systems. |
|||||||||||||||||||||||||||||||
|
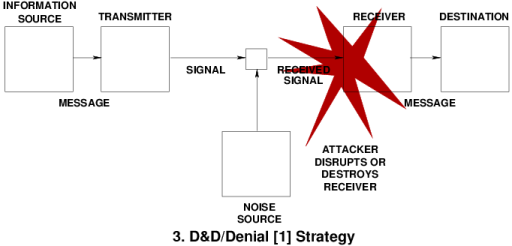
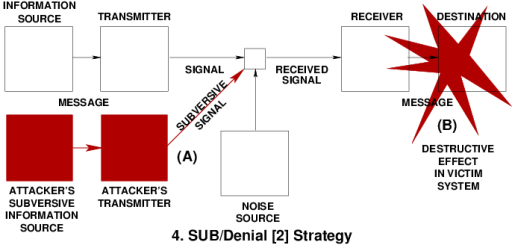
Deception in Biology: Nature's Exploitation of Information to Win Survival Contests |
|||||||||||||||||||||||||||||||
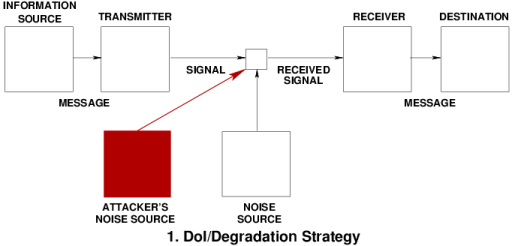 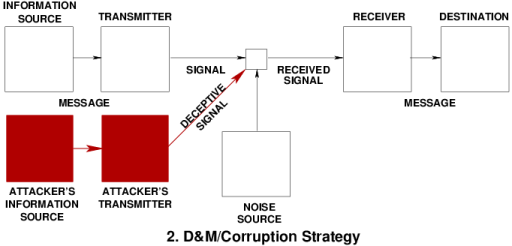   |
|||||||||||||||||||||||||||||||
|
Legacy Infowar Teaching Materials (2000-2006) |
|||||||||||||||||||||||||||||||
|
An
Quantitative
Introductory
Course
in
Information
Warfare
[Honours
Advanced
Module CSE
468
Information Conflict Semester 1 2006]
|
|||||||||||||||||||||||||||||||
|
|||||||||||||||||||||||||||||||
|
Theses and Projects |
|||||||||||||||||||||||||||||||
|
Lachlan
Brumley, HYPANT: A Hypergame
Analysis Tool, Honours Thesis, 2003, Monash University SCSSE (Website). |
|||||||||||||||||||||||||||||||
| HYPANT is a
hypergame simulator which implements the Fraser-Hipel algorithm for
hypergame analysis. The tool was implemented with the aim of producing
a
GPL code package suitable for use in more ambitious projects. |
|||||||||||||||||||||||||||||||
| Lachlan Brumley, PhD Project (Website). | |||||||||||||||||||||||||||||||
|
|
|||||||||||||||||||||||||||||||
 |
|||||||||||||||||||||||||||||||
 |
|||||||||||||||||||||||||||||||
|
|
|||||||||||||||||||||||||||||||
|
|||||||||||||||
| Artwork and text ¿ 1994 - 2010 Carlo Kopp; All rights reserved. |
| $Revision: 2.279 $ |