

| Information Warfare - Part 1 |
| Originally published December, 1996 |
| by
Carlo Kopp |
| ¿ 1996, 2005 Carlo Kopp |
| In this issue,
dedicated to security topics, we will digress from our established
technology base theme and take a look at the emerging problem area of
information warfare and info-terrorism, and some of the tools of this
trade and the technology issues involved. What is Information Warfare, and Who is at Risk? Information warfare is a sign of our modern times. The developed world has acquired a taste for computer and communications technology, and this as we can all appreciate, has also produced a significant dependency upon this technology. Where a dependency exists, a vulnerability also exists. Denial of basic computing and communications services today can be devastating to an economy, the machinery of government and well as a nation's armed services. Some industries, such as banking and finance, advanced automated manufacturing, or the chemical and petrochemical industries, cannot properly, if at all function if denied their computing, communications and networking infrastructure. The modern buzzword for paralysing, deceiving or disrupting an organisation through the disruption, manipulation or destruction of its information infrastructure is Information Warfare (IW). IW theorists recognise four classes of information warfare:
An example of the latter is a bomb or cruise missile aimed at a computer centre or telephone exchange. In perspective, there is nothing new about IW, all that has happened in recent years is that a formal nomenclature has been developed. We now have names and a more formal structure to describe practices, many of which have been around since the beginning of civilisation. If one wishes to push the paradigm, the processes via which a virus or bacterium bio-chemically deceives a defending cell into lowering its defences would also qualify as IW, albeit on a cellular level. Certainly modern military disciplines, such a Electronic Combat (the science and operational practices involved in jamming or busting up an opponent's radar and comms) is nothing less than a specialised form of IW, even if it had a name of its own for the last five decades. 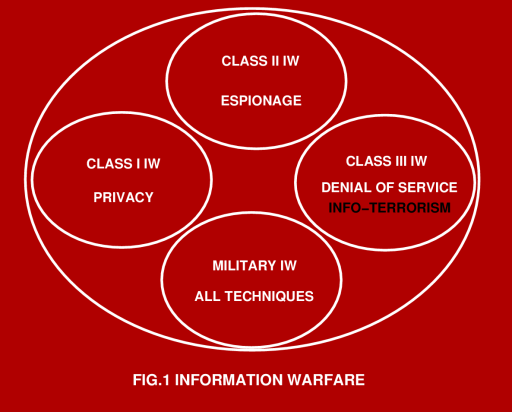 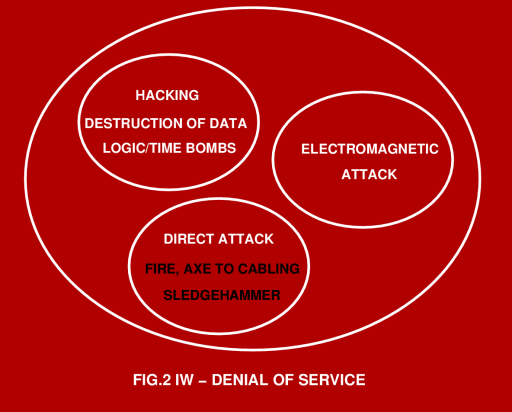 It is perhaps unfortunate that in the popular media and net culture IW has become synonymous with formally organised hacking, which is more properly known as "Gibsonian CyberWar", in honour of Gibson's sci-fi books on the "Cyber-Punk" culture. It is unfortunate because it distorts the common perception of what techniques may be employed by an IW practitioner against his or her victims. What must be understood here is that IW is ultimately about messing up the "thinking" processes of an opponent, and any means which achieve this will therefore qualify as IW. In this respect, those who assert that CyberWar and IW are one and the same have missed the essential and central point. From a computer industry perspective, IW is another ugly fact of life which many system administrators and IT managers will need to become very familiar with, if they are to be successful in protecting their employer's computational infrastructure from malicious third parties. The first and obvious question here is that of who is at risk and who isn't, and what is a measure of risk ? If we are to believe some in the IW community, then everybody is potentially at risk. In practical terms however, the organisations most at risk are those who deal with large amounts of money, either directly or indirectly through the economic activities they pursue. Banks, finance companies, insurers, large manufacturers and government departments are obvious examples. A good analogy here is that anybody who has a good reason to put anything into a safe or vault, or provide redundancy to ensure reliable service, is a potential target for IW. The measure of the risk one is exposed to is the value of what needs to be protected, and the number of weaknesses which may exist in the organisation's security, or more properly, defences. For an IW threat to exist, only two preconditions are needed. The first is the intent of a third party. The second is the capability to either penetrate or deny service. If we are to look for intent, we don't need to go very far. The first and obvious parties are criminal hackers, industrial spies and foreign governments with agendas of their own. If we look further, we will also find the categories of disgruntled former and current staff members, militant labour organisations, and the rather scary category of fundamentalist extremists. The latter may be religious and political zealots, "whatever rights" movements, Luddites, and national liberation movements (more commonly known as terrorists). Essentially, any nut-case with an agenda and the motivation to act upon it with malice, qualifies. The current focus of most activity in computer security is upon prevention of penetration, as a hacker can steal confidential information, eg credit card numbers, company plans, price-lists, customer lists and personal details entrusted to the owners of a system. This information can then be used either directly for profit, or indirectly to damage the victim organisation. Much less attention is typically paid to the area of denial of service, which in many instances can cause the victim far greater losses that the theft of bit and pieces of information. Info-terrorism and military IW have a strong emphasis upon the denial of service. This of course brings us to the central theme of this article, which is the subject of the vulnerability of the fundamental infrastructure to electromagnetic attack. The Vulnerability of the Infrastucture. The semiconductor is the heart of the information revolution. Of all the semiconductors in use, Silicon is by far the most important, playing a dominant role in both computers and communications. Silicon is a wonderful material, which allows the design and manufacture of fast, high density components. From a vulnerability perspective, however, Silicon has an unfortunate weakness. It doesn't like exposure to high voltages. Whether we look at low density bipolar transistors, or high density Metal Oxide Semiconductor (MOS) components, they all share a common attribute - if you expose them to voltages in excess of the several Volts or tens of Volts to which they are rated, they die a horrible death. In bipolar devices, reverse biased junctions suffer an effect called avalanche breakdown, which will typically cause large currents to flow through a device. In many instances this current will damage the junction, if not causing melt-down then certainly causing lesser thermal damage. In MOS devices, a high voltage applied to the transistor Gate, which is essentially a miniature capacitor, will cause the catastrophic dielectric breakdown of the Gate. In most instances the Gate will develop a permanent leak which will degrade performance, often to the point where the component no longer functions. What is very important in both instances is that a miniscule amount of energy is usually required to cause a breakdown, once this has occurred the power supply in the equipment does the rest of the work, dumping the main capacitors' charge into the hapless component. A good example would be computer power supplies with tens of thousands of microFarads at 5V, typically containing of the order of a Joule of energy. If you dump a Joule into any structure which is microns in size, it will typically vapourise. A good example here is damage caused by static electricity. A fascinating case study is a problem the American military experienced during the 1991 Gulf War. Static electricity accumulated on radio aerials, the result of statically charged sand particles in a dust storm hitting the antenna, was sufficient to cause breakdown in the semiconductors in the transmitters and receivers in the equipment. As semiconductors are highly susceptible to high voltages, any means via which such voltages can be injected into a piece of equipment can be used as a weapon to disrupt, damage and destroy the equipment. The question to ask in this context is that of how dangerous high voltages can be coupled into equipment to cause damage. Needless to say, a wide range of means exist and many have been exploited for exactly this purpose. To understand the means via which damaging voltages can be coupled, we must look at the infrastructure from the perspective of the basic physics and electrical theory of antennas, transmission lines and shielding. Regulatory requirements on electromagnetic interference mean that most computer and networking equipment today has some measure of shielding, which is typically implemented by enclosing equipment in metal cases, metal lined plastic cases or metal coated plastic cases. This shielding is designed to keep milliVolt or microVolt level radiation from escaping the equipment and putting stripes on neighbourhood television sets. As most readers will appreciate, in practice such shielding doesn't always perform well, and the common commercial el-cheapo PC will usually manage to do exactly what is not needed. Even higher quality equipment such as fileservers, minis and mainframe size systems will often leak, often because people can't be bothered to tighten all the panels on the chassis. Often panels are not installed at all, particularly where an SCSI or serial cable needs to be run in or out of a chassis which doesn't have all of the appropriate holes on its back panel. Antenna theorists recognise what is called the reciprocity theorem, which essentially says that any transmitting antenna also behaves as a receiving antenna. What this means is that any chassis which leaks radiation from inside will also leak radiation from outside in, if the equipment is placed into an external electromagnetic field. If you illuminate such equipment with a microwave field strength of kiloVolts or tens of kiloVolts per metre, energy will leak in and may be capable of causing genuine damage, if not a crash or a reset. Shielding is however a minor vulnerability, in comparison with the behaviour of network and power cables. Both networking and power cables usually involve runs of tens to thousands of metres, and these usually comprise multiple linear segments at right angles to one another, as they follow corridors and risers. What this means is that they can be very good omnidirectional wideband receiving antennas. Radiation of wavelengths from tens of metres to centimetres can often couple very effectively from any direction. Moreover, energy can couple across from one cable to another, if they are running in the same duct or tray. Needless to say, if an electromagnetic field of appreciable strength impinges upon a site, it will produce appreciable voltages in such wiring. These voltages, following the physics of transmission line theory, will propagate along the cable at the speed of light and typically form high voltage standing waves on the cable. Since a piece of equipment is typically hanging off either end of the cable, it will be exposed to a radio frequency high voltage. Electromagnetic weapons theorists call this effect back door coupling, as energy is introduced into the victim equipment "via the back door". Of particular concern are networking cables, as these typically use fast low loss dielectrics, which of course do a very efficient job of propagating RF signals through a site. This is indeed what they are designed to do, and a 100 Base T cable will have a bandwidth into the hundreds of MegaHertz (metres to decimetres of wavelength) simply in order to carry its legitimate network traffic. Once high voltage RF gets into a piece of equipment, anything can happen from a reset or logic malfunction, up to the electrical damage and subsequent burnout of electronic components. Since we only need tens of Volts to toast a micro or a DRAM chip, letting anything up to kiloVolts of RF loose inside a computer can and usually will damage if not kill the machine dead. If the equipment uses isolation transformers on its networking ports, then the issue is whether these can withstand the stress produced by the voltage. In many instances they will not and thus short through. It is also entirely possible that some will be quite leaky to RF voltages through internal stray capacitances, and thus while stopping the effects of a power surge, they will not stop an RF attack. 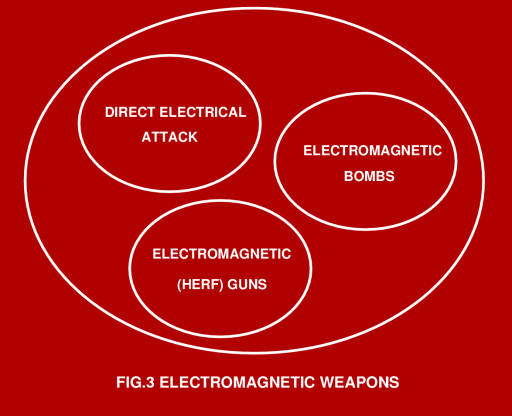 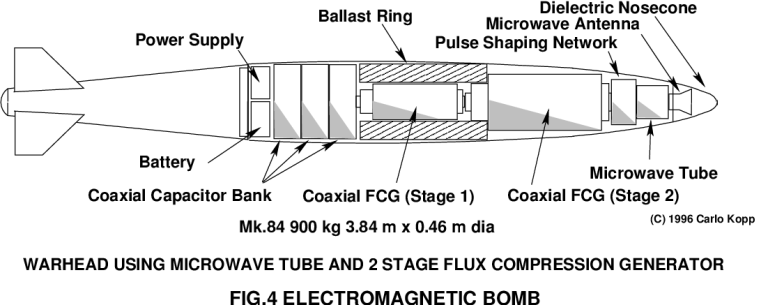 Electromagnetic Weapons Whilst any device capable of producing a powerful electromagnetic field can be used as an electromagnetic weapon, a number of quite specialised devices have evolved in recent years for exactly this purpose. Other devices can be used as improvised electromagnetic weapons. A very good example of the latter is the famous Tazer stun gun, of Dirty Harry "Enforcer" fame. This device shoots out a couple of wires with sticky pad contacts on the ends. Once these are attached to a victim, the user squeezes the trigger on the Tazer, letting loose a 50 kV high voltage into the victim. Guaranteed to paralyse if not kill a weak hearted victim. Consider however the effects of connecting a Tazer into a wall socket LAN port, using a home built RJ-45 or BNC attachment. Fifty kiloVolts will punch through every isolation transformer on the network, and more than likely not only take down a hub/repeater/bridge, but also any other pieces of equipment attached to this node. The likely outcome of a Tazer attack is the devastation of all networking hardware connected to the LAN, network adaptors on all hosts, and if you are unlucky, also a lot of hosts with other electrical damage. Tazers are a nightmare for security engineers in the US, because they are a widely available item. A less destructive improvised weapon is the Tesla coil. Devised by the brilliant if somewhat weird Nikola Tesla, the inventor of the triple phase AC electrical system we all use today, the Tesla coil is a resonant RF high voltage transformer. Telsa coils are these days typically used as disco curiosities, intro pictures for X-files and kooky UFO believe it or not shows, or as a lab tool for testing vacuum. It also turns out that such a Tesla coil will cause a PC to crash or hang from a distance of anything up to ten metres. A bigger Tesla coil will do this from a greater distance. Since small Tesla coils are low energy devices, they are unlikely to produce permanent damage. Imagine however the effects of somebody hiding a Kambrook timer operated mains powered Tesla coil into a cleaner's cupboard or above a ceiling panel, down the corridor from your computer room. Unless you find it by accident, you will have no idea why your systems are crashing, moreso if the bad guy is smart and sets the timer in random mode, only to run for a few seconds at a time. You would have to tear the building apart to find it. From improvised weapons we can now move up to purpose designed ones. The foremost of these we need to be concerned with is the HERF (High Energy RF) gun. A typical HERF gun can be built simply by bolting a one metre UHF band Yagi antenna, the type you use for SBS TV, on to a rifle stock, and feeding the antenna dipole from a backpack UHF pulsed transmitter. The backpack will contain a battery, a master oscillator, a UHF power tube and tuned circuit, and a high voltage power supply to drive the tube. The HERF gun will need to put out a few kiloWatts of peak power, but this is certainly doable with off the shelf technology. If you want to be very destructive you can also move into the microwave band, and use a helical antenna and a tube from a microwave oven. Military forces and law enforcement agencies in US are already deploying HERF guns. The latter devices are claimed to be capable of taking down the electronic ignition system of a motor vehicle from a hundred yards. A top of the line HERF gun would use a pulsed high power microwave tube capable of producing hundreds of kiloWatts of peak power. This would allow an info-terrorist to take down a site simply by firing the HERF gun through a window several buildings away. Since electromagnetic waves penetrate windows and walls quite well, hiding your machine room in the middle of th building may not help. If the HERF gun sounds scary, then you are in for a bigger fright. The electromagnetic bomb is far more destructive. Electromagnetic bombs are on the verge of military deployment, as warheads for missiles and aircraft delivered bombs. Arguably, a backpack packaged electromagnetic "limpet mine" is also feasible. Electromagnetic bombs are powered by a device termed a magnetic flux compression generator (FCG), invented at Los Alamos during the fifties, which uses a fast high performance plastic explosive to compress a magnetic field in an inductor. The force of the explosive transfers an enormous amount of energy into the field. The largest flux generator the author has seen published produced a peak current in its electrical winding of 150 million Amps for about 20 microseconds. This is about 50,000 times the current in a typical lightning stroke. More typical flux generators produce millions to tens of millions of Amps of current, delivering peak power outputs of TeraWatts (10^12 Watts). Even so, the magnetic fields in the near vicinity of such a device are so powerful that they will produce high voltage spikes on wiring, as well as penetrate directly through most computer chassis shielding, and erase most magnetic materials. As a result, a reasonably big flux generator will toast every piece of electronics in a radius of tens to hundreds of metres (for more detail see Winn Schwartau's second edition of CyberWar and Info-terrorism, published recently by Thunders Mouth Press in the US). Understandably, this can be improved upon from an attackers perspective, by using the generator to drive a microwave tube. Suitable tubes exist which can produce brief pulses of up to GigaWatts or tens of GigaWatts of microwave power. Such weapons can blanket an area of up to hundreds of metres in diameter with field strengths of kiloVolts to tens of kiloVolts per metre. It is for good reason that electromagnetic bombs are commonly described as the nuclear weapons of the information age. We won't bother looking at nuclear EMP bombs since it is unlikely that much would survive the circumstances of their use. Interested readers should see the documentary film "Trinity and Beyond" for more detail. Are you scared ? If your site fits the profile of a likely target, and you haven't hardened it properly against electromagnetic attack, then you certainly should be scared. Next issue will look at hardening and defensive measures against electromagnetic attack. |
| $Revision: 1.1 $ |
| Last Updated: Sun Apr 24 11:22:45 GMT 2005 |
| Artwork and text ¿ 2005 Carlo Kopp |
